

ADSB on Kubernetes
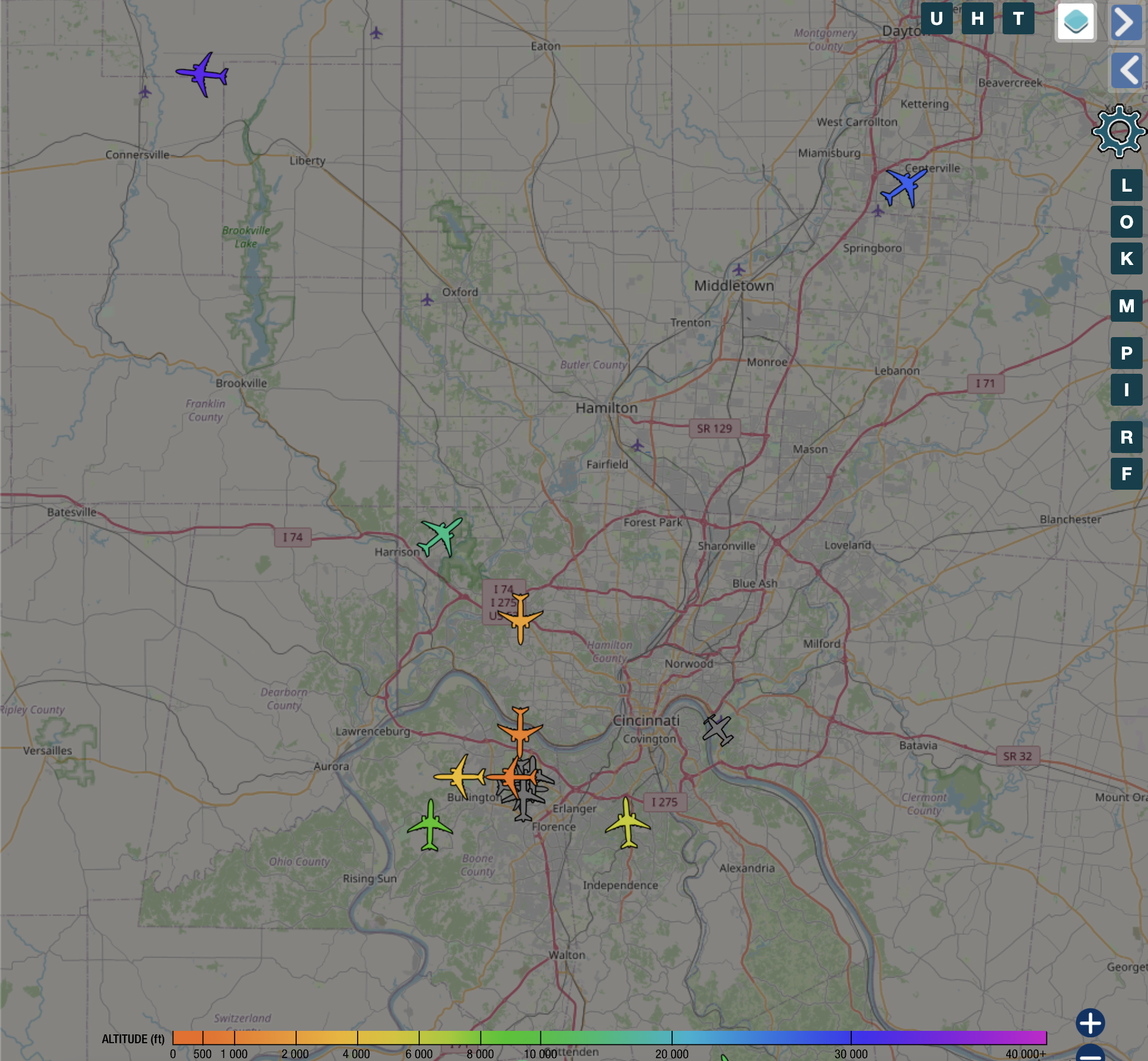
Setting Up an ADS‑B Flight Tracker with a Cheap Antenna on Kubernetes (RKE2 and ArgoCD) This is the Kubernetes version of my earlier Docker‑based ADS‑B guide. In this setup, everything is defined in YAML and deployed via ArgoCD, and changes are tracked in Git and synced automatically to the cluster. Access is handled through an NGINX Ingress with TLS from cert‑manager, which is how I publish the ADS‑B UI at adsb.w3rdw.radio. If you’re comfortable editing YAML and committing to Git, you’ll feel right at home. ...

Using a New NTLM Hash Lookup Bulk Check API
Using a New NTLM Hash Lookup Bulk Check API In today’s cybersecurity landscape, organizations and security professionals are continually searching for efficient ways to detect and mitigate threats. One such method involves using NTLM hash lookup services. If you’re looking to validate multiple NTLM hashes quickly, a bulk check API can be invaluable. In this post, we’ll delve into the specifics of using a NTLM hash lookup bulk check API and guide you through the process. ...

ADSB
W3RDW Blog - First Post This post is copied from a separate site where I plan to document content related to one of my hobbies, HAM radio. This post is the first post I shared on my other site, https://w3rdw.radio. In the future, I plan to only post HAM radio content on the W3RDW site. You can find a link in the top right corner of my WhiteMatterTech site. Setting Up an ADS-B Flight Tracker with a Cheap Antenna and Docker on Ubuntu In this tutorial, I’ll walk you through the process of setting up an ADS-B flight tracker using a cheap antenna and Docker on Ubuntu. ADS-B (Automatic Dependent Surveillance – Broadcast) is a surveillance technology that allows aircraft to determine their position via satellite navigation and periodically broadcast it. By setting up your own ADS-B receiver, you can track flights in your area and contribute to the global flight tracking network. ...

A Roadmap to a Rewarding Career in Cybersecurity: A Guide for Beginners
Introduction Are you considering a career in cybersecurity? That’s a fantastic choice! The world of cybersecurity is dynamic, challenging, and highly rewarding. Whether you’re a recent graduate or someone looking to make a career change, there’s a place for you in this ever-evolving field. A cybersecurity bootcamp student recently reached out to me on LinkedIn to ask exactly how to do this. In this post, I will share some of my advice in a more blog-friendly format. I’ll walk you through some steps to break into the cybersecurity industry successfully. ...

Unlocking Digital Transformation: The Crucial Role of IT Services
Introduction In today’s rapidly evolving business landscape, digital transformation has become more than just a buzzword—it’s a strategic imperative. Organizations worldwide are harnessing technology to enhance processes, elevate customer experiences, and stay ahead in the competitive race. Amid this digital revolution, IT services emerge as indispensable allies, guiding and empowering organizations in their transformative journey. Let’s explore how IT services play a pivotal role in driving this essential shift. 1. Technology Assessment and Planning IT services providers begin by meticulously evaluating your existing IT infrastructure, systems, and processes. Through this comprehensive assessment, they identify gaps, recognize untapped potential, and craft a well-defined roadmap for your digital transformation endeavors. ...