Interestingly, after my previous post describing how to route Docker containers through VPN on Unraid, I received a substantial lot of questions via email about my hints at accessing Twitter anonymously. This post is my response to those questions, and I will describe my workflow to access Twitter feeds anonymously, without an account.
This post will assume you have read my post on how to route Docker containers through VPN on Unraid or that you already know how to accomplish this. If you do not, start here.
I will be using Unraid in this tutorial, but you could accomplish the same functionality with Docker on another host OS.
Nitter
The Docker container used to access Twitter is a wonderful third-party tool known as Nitter (zedeus/nitter). This container is relatively self-explanatory, but the purpose of the container is to be able to search for your favorite Twitter users and see their feeds.
All requests go through the backend, and your client never talks to Twitter, which is how Nitter prevents Twitter from tracking your IP or JavaScript fingerprint, thus enhancing privacy. Behind a VPN, you have yourself a self-hosted, anonymous Twitter reader that does not require an account or track you.
There are also public Nitter instances you could use if your prefer not to host your own instance: https://github.com/zedeus/nitter/wiki/Instances. But don’t you want to use your reverse proxy to route twitter.your-domain.com to your Nitter instance and have your own Twitter?
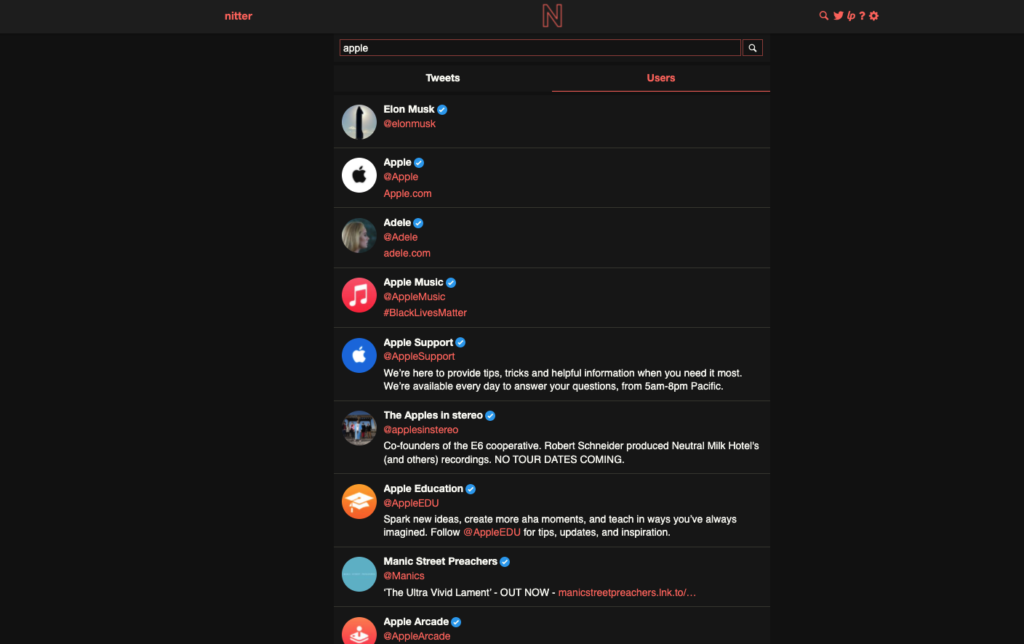
Example Nitter Search for “Apple”
Search for your favorite user(s), select their profile, and click the RSS icon in the top right corner of the screen. Copy the URL of the RSS page for use in the next steps.

Click the RSS Icon
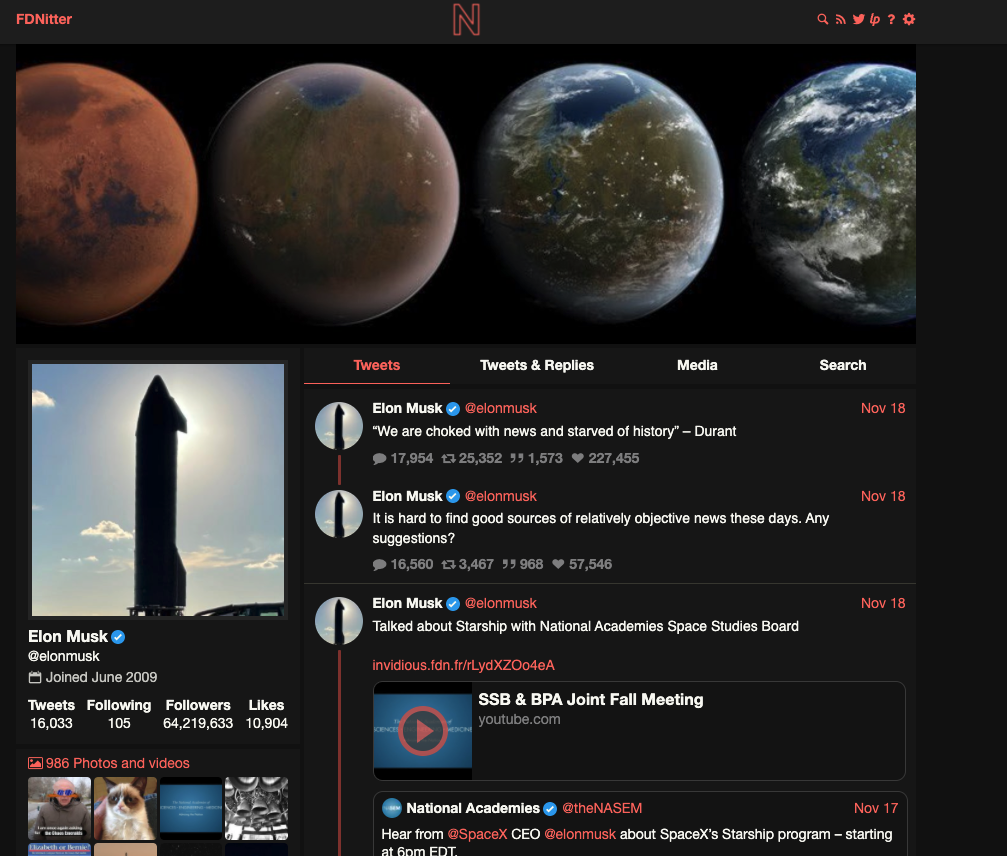
Example User Account on Nitter, of your favorite Elon Musk
FreshRSS
Now, in conjunction with your Nitter container behind a VPN (or simply a public Nitter instance like mentioned above), add FreshRSS (linuxserver/freshrss). This container will allow you to maintain the records of the feeds you want to follow in the form of RSS.
Even if you choose to only use this container to access a locally hosted Nitter instance, I still recommend routing it through a VPN. There may come a day where you open your Nitter container publically or where you decide to grab RSS feeds from elsewhere. In either case, a VPN will help provide anonymity and security, making it even harder for trackers to store your data.
Once the container is launched, select “Add a feed or category” on the left navigation panel. Under “Add a category,” you can create your own categories to keep your feeds organized (e.g., Tech, Politics, etc.). Under “Add a feed,” you can begin adding the feeds from Nitter that you want to follow. In my screenshot below, you can see I am using a public Nitter instance and attempting to follow Elon Musk (https://nitter.fdn.fr/elonmusk/rss). Add the URL in the “Feed URL” section, select a category that you have made previously, and click “Add” to confirm. If you want to add even ANOTHER layer of privacy, you can also set up a SOCKS5 proxy connection as shown in the screenshot. If using Unraid to host your SOCKS5 proxy server, it would look something like the screenshot below.
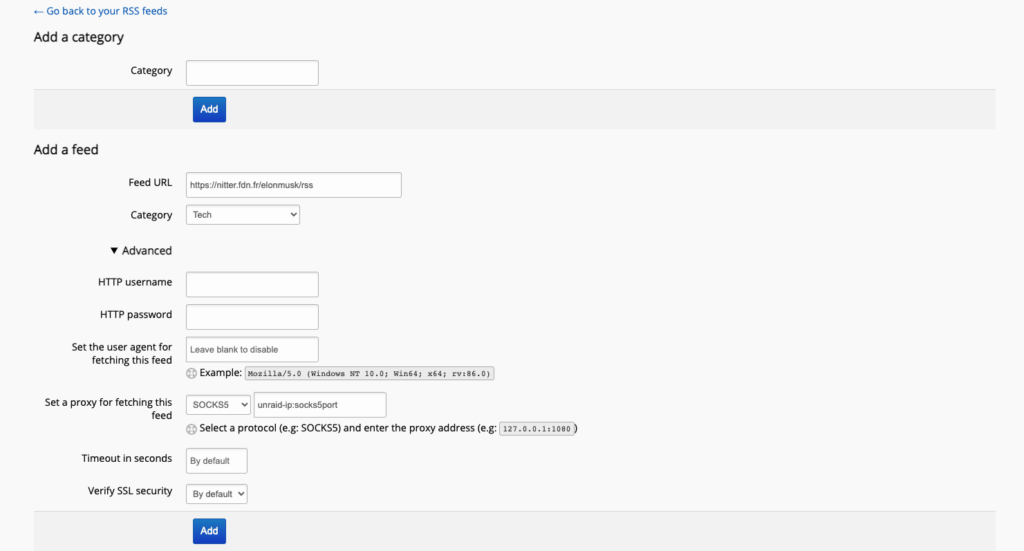
Even with FreshRSS, you can consider using your reverse proxy to route something like rss.your-domain.com to your container.
I would highly recommend setting up HTTP auth via your reverse proxy if you plan to open either of these containers to the public. Strong authentication will be invaluable in such a case. As always, I recommend the use of a password manager in order to generate, store, and access strong credentials (I use 1Password currently).
Conclusion
Congratulations if you made it this far and everything is working! I hope this tutorial aids you in your endeavors to anonymize your access to Twitter while substantially enhancing the privacy and preventing tracking of your personal data.
As always, if you have any questions, feel free to start a Discussion on GitHub, submit a GitHub PR to recommend changes/fixes in the article, or reach out to me directly at [email protected].
Thanks for reading!
Robert
