ADSB
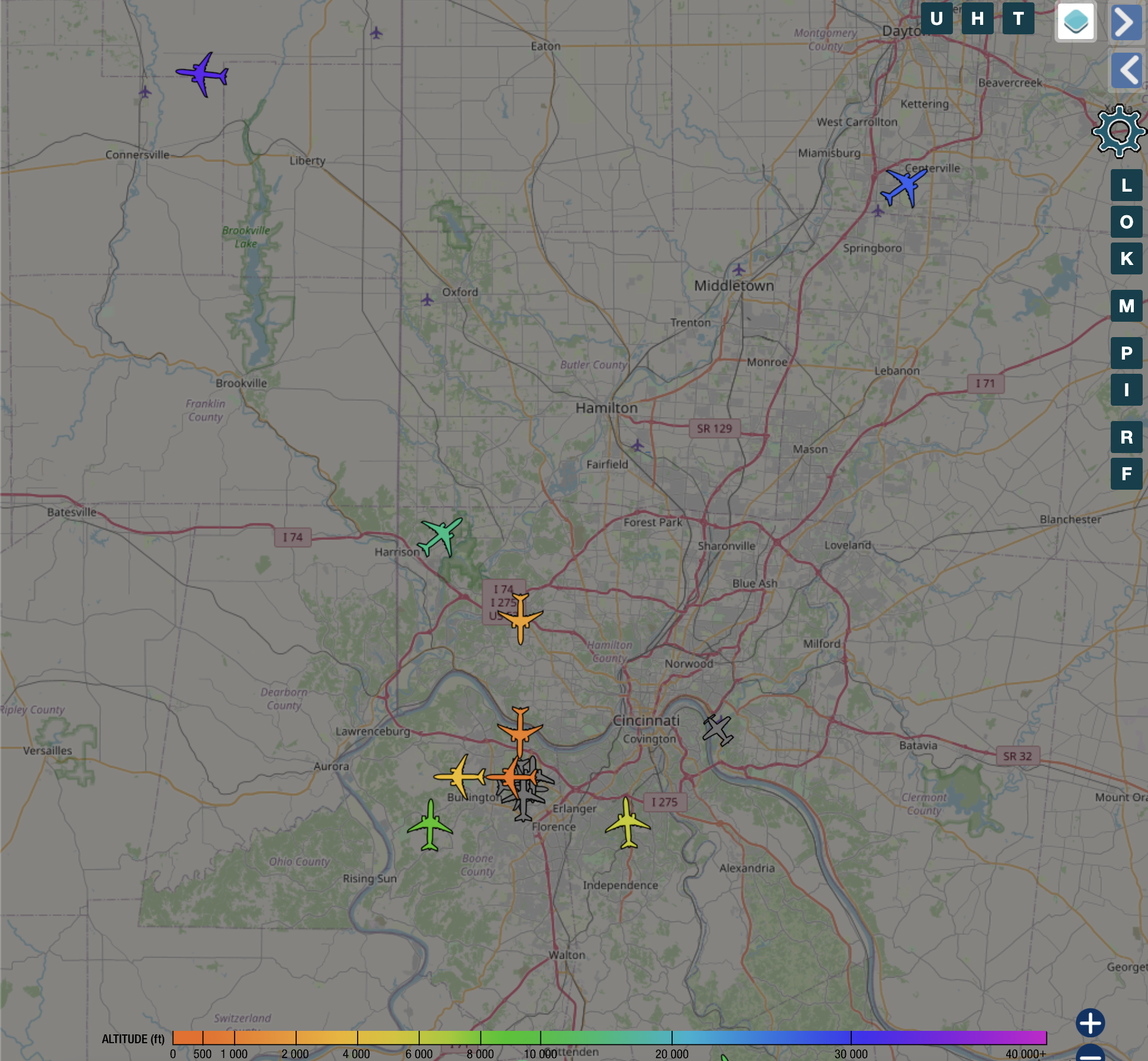
W3RDW Blog - First Post This post is copied from a separate site where I plan to document content related to one of my hobbies, HAM radio. This post is the first post I shared on my other site, https://w3rdw.radio. In the future, I plan to only post HAM radio content on the W3RDW site. You can find a link in the top right corner of my WhiteMatterTech site. Setting Up an ADS-B Flight Tracker with a Cheap Antenna and Docker on Ubuntu In this tutorial, I’ll walk you through the process of setting up an ADS-B flight tracker using a cheap antenna and Docker on Ubuntu....